Well just another day in the IT world right ? Another day, another breach. What’s going on is the failure for executive buy in on security architecture and training changes. What happens is that people get stuck and resistant to change in habits, mindsets, and fiscal disciplines. That conversation with a client to pursue training for end users is a must. Most of the responses we hear are not to invest in training. Colonial Pipeline may have responded not to invest as much in training with proven breach prevention platforms, but we’re not sure. How could a company that has existed for so long not have a mature security program? The attack surface is found in the end user these days and improper configurations of security devices or in this case computing devices as well. This is definitely going to strike a cord in many job roles as we have fundamental breakdown in execution of security policy.
The corporate level executives have governance and compliance issues to measure and close the gaps found between where they are and where they should be. This is called a POAM Plan of Action and Milestones in a risk assessment periodic review (If they have a good security program). The whole point of security as a process is not to come up with the best defense ever but the best approach to defense around business goals and available funds for technology. In time grow from there as funds and business needs change. The attacks are going to happen. If you are reading this you are a target or the next target. Better yet, you are a victim and you just don’t know it yet.
Image below of those responsible for allowing this to happen
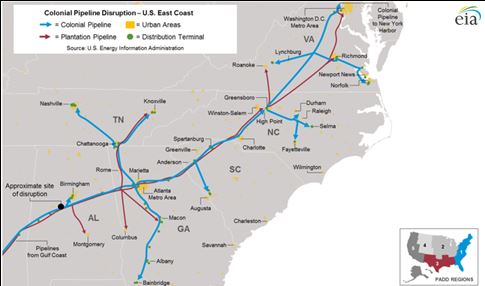
So how did the attack go down ? We’ll keep you posted as more information comes in. Most likely an end user, or an IT person with privilege level access operating in a way they should not have been. A company working in the fossil fuel business around since 1962 does not fall on its face like this without an inside job. Either that or their focus is grossly misplaced.
What could have been done to prevent this ? Implementing Palo Alto Networks next generation firewall that has the latest features including machine learning capabilities to spot and stop 0 day attacks. coupled with App-ID, user-ID, PANDB-URL, DNS Sink Hole implementations, Wildfire, and file blocking could have seriously thwarted this attack. We would have suggested also to be using the latest EDR protection for endpoints. This could have been from Cortex or even Crowdstrike. While these solutions offer protection, it comes down to people and process to ensure they are implemented, and implemented correctly. Even so much as reviewed by trained human talent over logging and verification that tool are operating as they should.
Now for opinion – Is this a political event to further push prices against Americans? Are businesses like oil industry and lumber looking to make a buck $ and claim as much of that stimulus money ?